
Good old games, good old vulnerabilities

Hello there. As you might guess by the title, this article is another description of vulnerabilities in game launchers, like others where I test Steam and Origin. Today we are talking about the GOG Galaxy launcher from CD Project RED.
I almost forgot about this research by now, but the recent news that Cyberpunk 2077 was available to pre-download in the launcher reminded me that I haven’t publicly shared my research. This is a bit of a strange story, because I don't even know how it ended - more on that below. I’m going to tell you how it was going.
Research
14 july 2019. I tested various launchers and decided to dig into the GOG Galaxy client for Windows. At the time of the research, the version was 1.2.57.74. Even then, there was GOG Galaxy 2. But it was in beta and an access was limited.
I noticed that the launcher installed two services for its working: «Galaxy client service» and «GalaxyCommunication». I skipped the first one, because the second service immediately caught my attention.
The service was located at C:\ProgramData\GOG.com\Galaxy\redists\GalaxyCommunication.exe, it worked as a highly privileged NT AUTHORITY\SYSTEM user and any user could start and stop the service.
Folder permissions (ACL) are standard for C:\ProgramData:
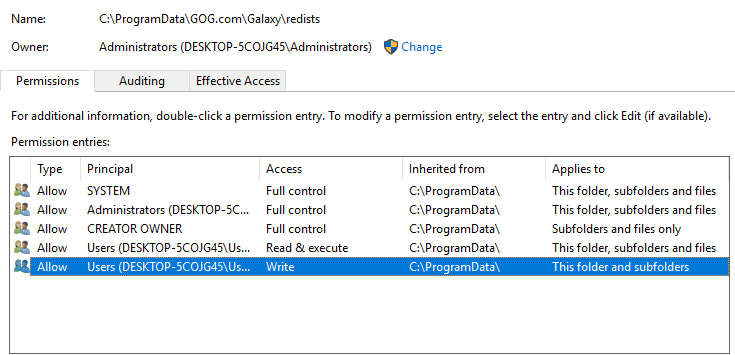
Thus, all the conditions for the dll hijack attack were created. The rights to the folder did not allow us to change the contents of GalaxyCommunication.exe, but allowed to put some library there, for example iphlpapi.dll.
I created simple PoC (proof of concept) and instruction: copy the library, restart the service. That's how any user could get the maximum privileges. Then I sent those altogether to GOG Galaxy support.
8 october 2019. We sent few letters to each other, the point of which was the fact that the vulnerability has been confirmed and the fix would be included in the next version 1.2.60.
I checked that the service was disabled in the 1.2.60 beta client and couldn’t be enabled without administrator rights, so the vulnerability was fixed. The service was removed later.
9 october 2019. I made an additional research on the launcher and found two extra vulnerabilities. One was "easy", the other was "complicated". I prepared a description for the easy one:
There was a file C:\ProgramData\GOG.com\Galaxy\communication_config.json with custom ACL “Everyone – Full Access”. We were able to delete the file and to create a hardlink with the same name pointing to any other file. I chose C:\Program Files (x86)\GOG Galaxy\GalaxyClientService.exe (service executable file). After the service restarted, it changed ACL of the service executable through hardlink. After that it was possible to change content of the executable and run any code as NT AUTHORITY\SYSTEM.
A "complicated" vulnerability allowed to send a request from the user level that behaves the same as in the case above, but working directly with the arbitrary file without hardlinks being used. But the preparation of the PoC was slow, so I sent a brief description to support.
10 october 2019. I was told that the issue was reported by another researcher and the fix is on its way.
26 november 2019. Version 1.2.62 was released with a fix for the CVE-2019-15511 (https://github.com/adenkiewicz/CVE-2019-15511) vulnerability. As I expected, there was a simple local-network API that allowed the user to request a service of making changes.
Unfortunately, neither the "easy" vulnerability nor the "complicated" CVE-2019-15511 were fixed. The developers added only a field into the request with a special code that service checks.
As a legal software can calculate this code from the user level, then PoC also can.
28 november 2019. I provided a PoC that changed the ACL for an arbitrary file even for the "patched" version.
And… actually that’s all. This is how our communication ended. I requested CVEs for 4 reported vulnerabilities (3, in fact, because one CVE had already been assigned) several times, but no luck. Support told me that they had started obtaining CVEs, but encountered problems with requesting, and other empty words.
At that time, I did not know what and where to check, because GOG Galaxy 2 was publicly released as GOG Galaxy replacement. As far as I understand, all the vulnerabilities described are applicable to it and I do not know the version of the product, so it makes no sense to request a CVE for an unsupported old software. Therefore, I dropped the situation with the thoughts that, as the agreed 90 days pass, I would simply publish everything I found. Due to the agreed period came to an end (which is obvious, because I’ve totally forgot about it), I publish the vulnerabilities and its descriptions.
Summary
So, I found and reported 4 vulnerabilities of GOG Galaxy client for Windows.
1) Dll hijack in old version of GOG Galaxy;
2) ACL set «Everyone – Full Access» due to hardlink;
3) ACL set «Everyone – Full Access» due to custom request (CVE-2019-15511);
4) Bypass fix CVE-2019-15511.
Most likely, only first and third vulnerabilities from the list were fixed. Second and fourth ones are still applicable (but I can’t be sure, because I didn’t test it). So, users who use the GOG Galaxy, should be careful, most likely your computer can become not yours easily.
